Release Notes Through 2024-05-09
Overview
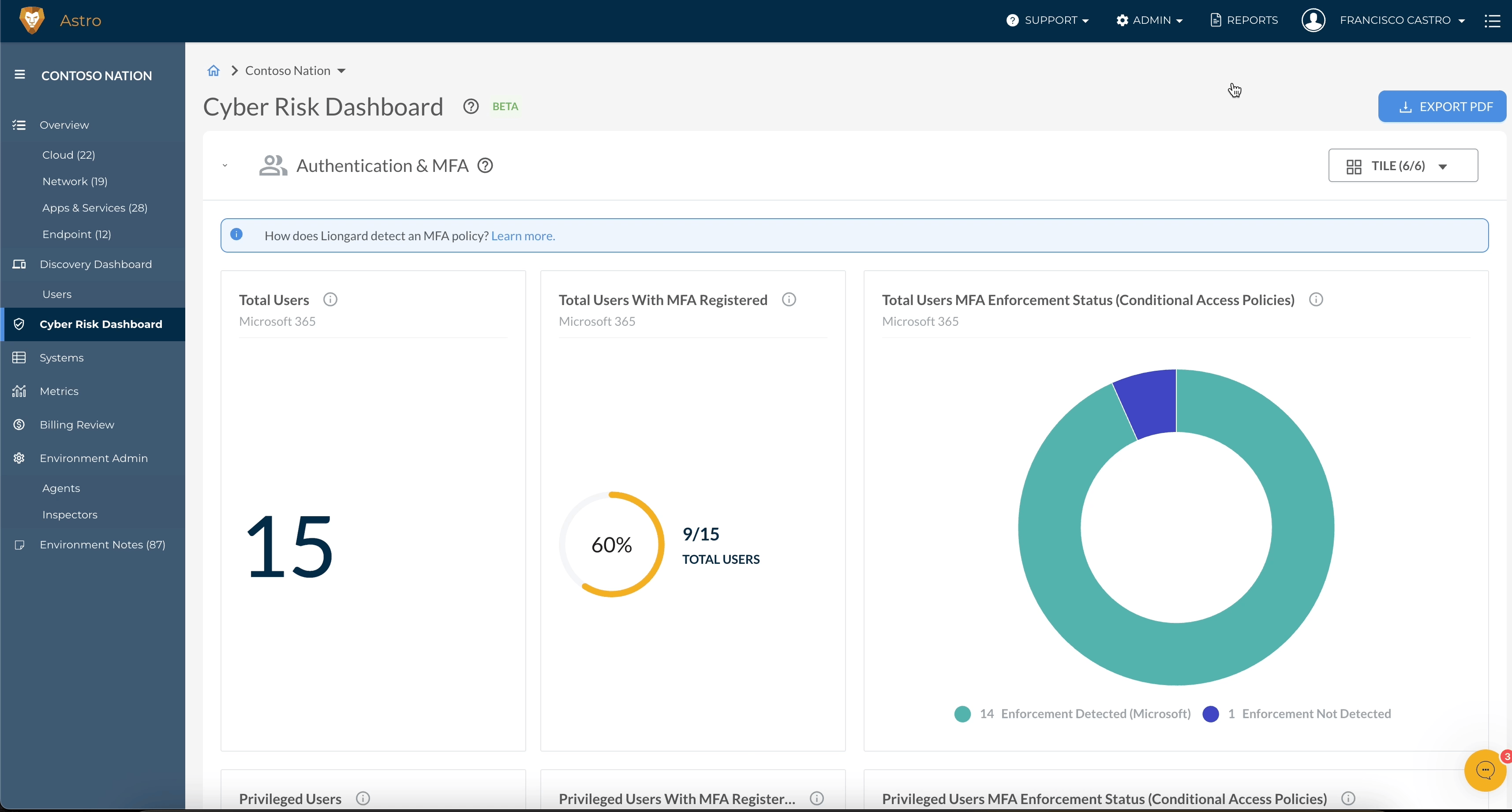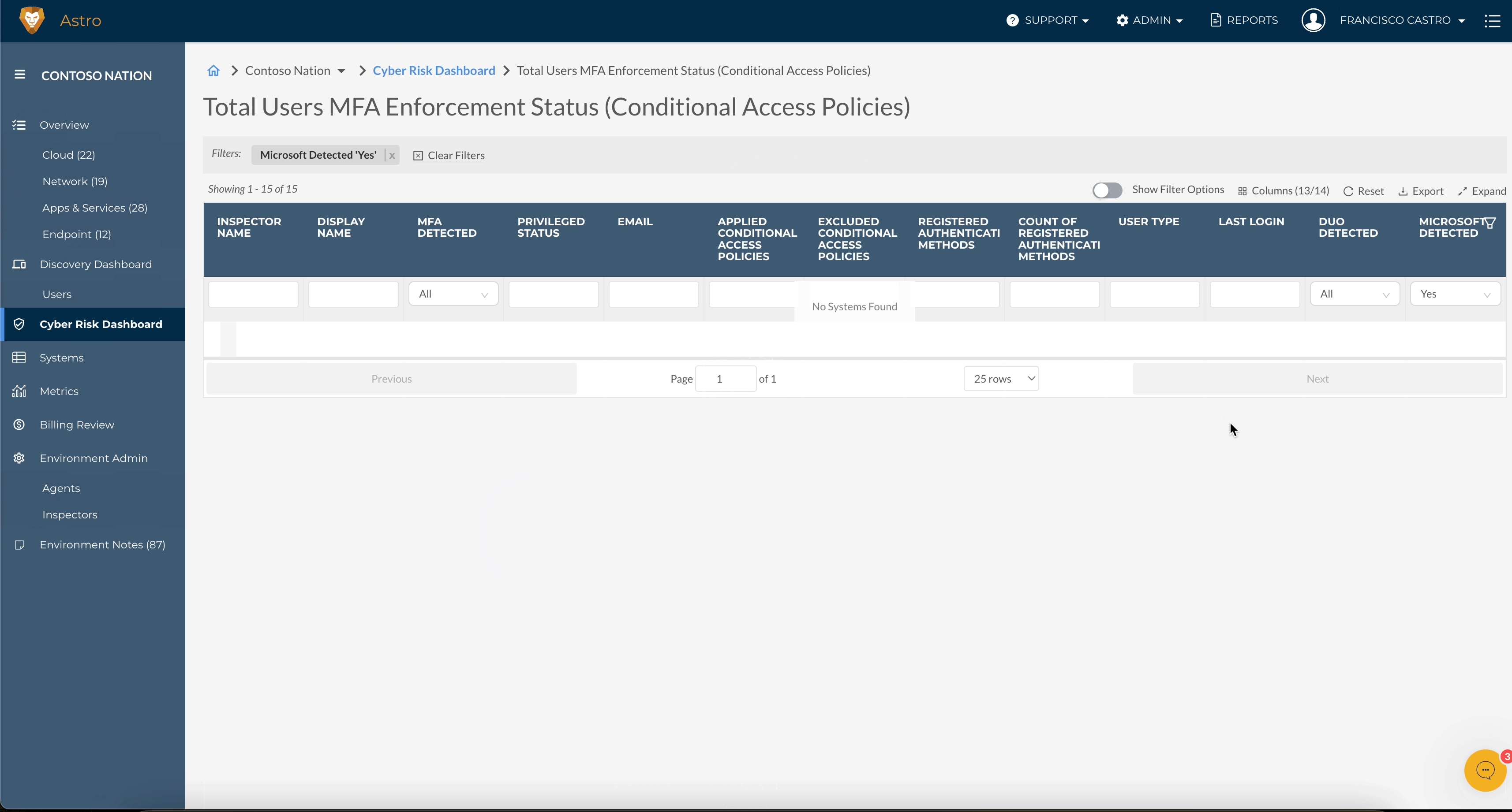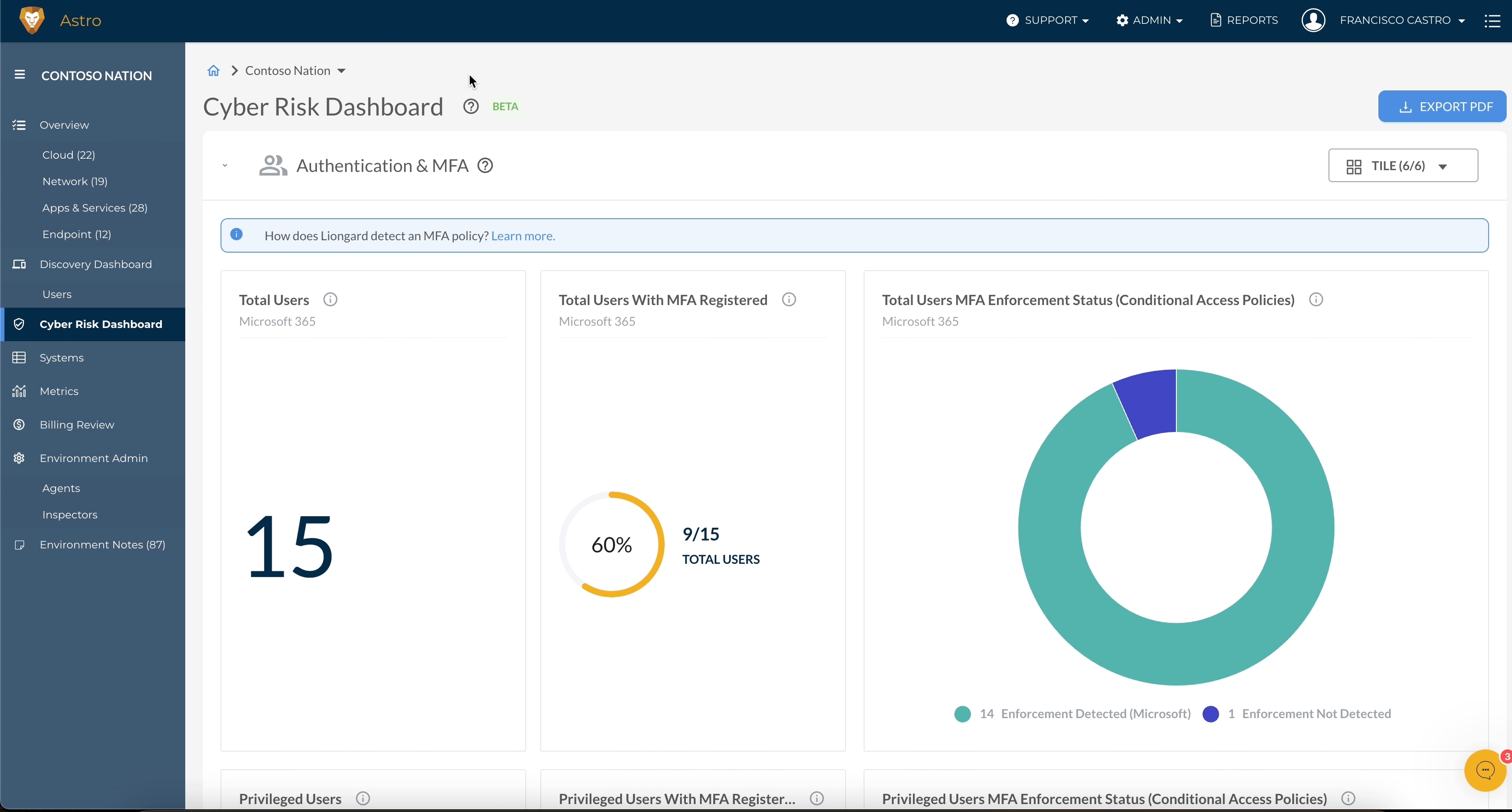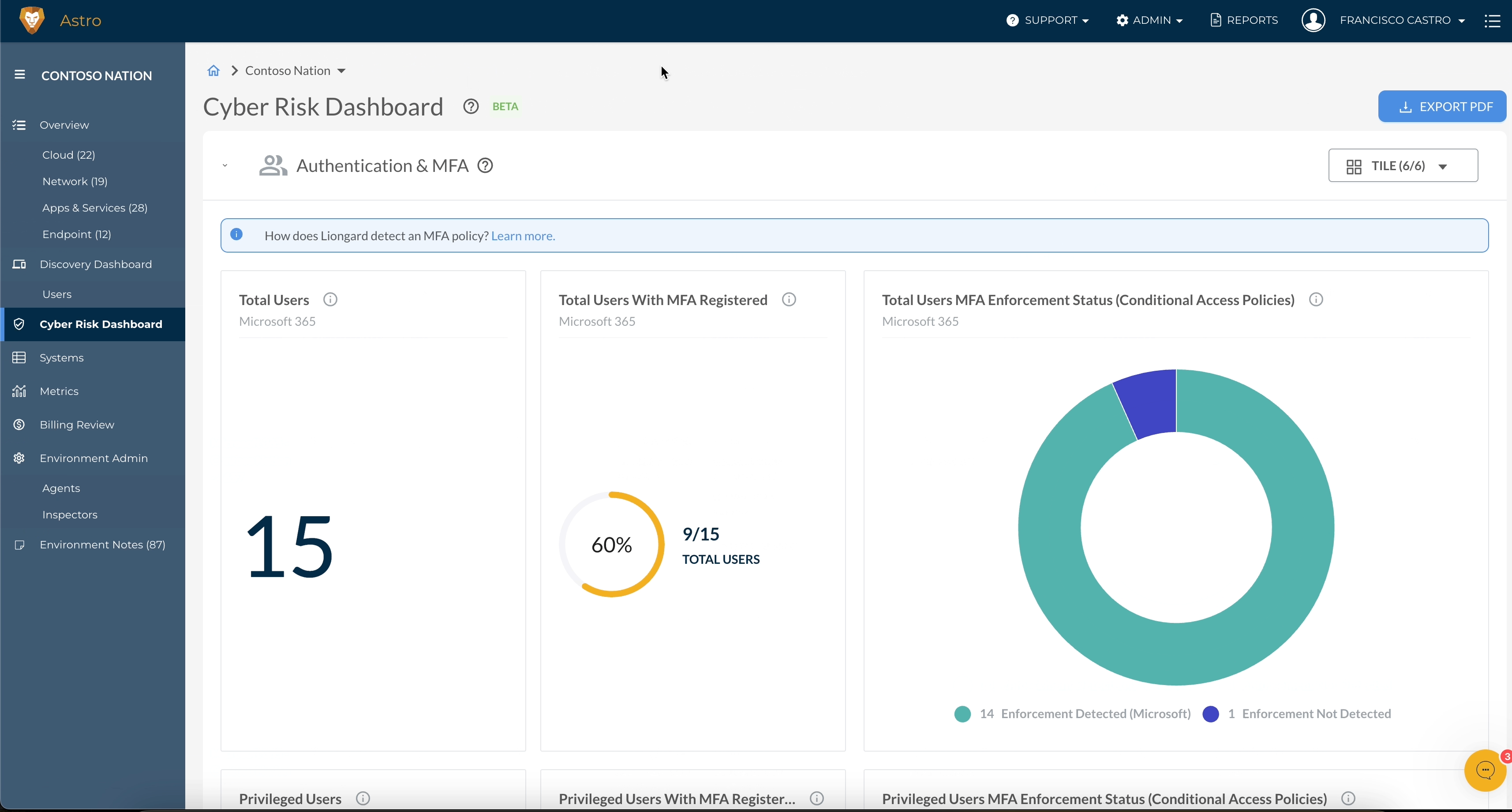
Support for Data on MFA Enforcement via Conditional Access Policies Now Available in Cyber Risk Dashboard
Partners that utilize default Conditional Access Policies for MFA Enforcement in Microsoft 365 can now track MFA enforcement and compliance using the Cyber Risk Dashboard. The Cyber Risk Dashboard now surfaces key insights on MFA Enforcement via Conditional Access Policies that use the following Entra ID access grants:
- Require multi-factor authentication
- Require authentication strength
- RequireDuoMfa (if configured)
These new insights enable you to easily track and enforce your user access management security standards in Microsoft 365. For more information, visit our Microsoft MFA FAQ article to learn about what Microsoft 365 multifactor authentication data Liongard supports.
Huntress Inspector (Beta) is Now Available in all Instances

Introducing the beta release of the Huntress Inspector for Liongard! This integration allows Huntress agent statuses to be monitored directly within Liongard, streamlining historical data tracking, change detection, and alert creation. Plus, non-admin users gain access to critical information, enhancing team-wide awareness and improving security management and operational efficiency.
The new Huntress inspector features:
- Reports in the form of data-view tables display information about agents' and hosts' endpoints' status.
- Summaries of key data points to provide a simple snapshot of the state of deployed Huntress agents.
- Tracked changes in deployed agent statuses over time and the ability to create alerts on these changes.
For more information on this Inspector and its configuration, please visit our documentation.
What is Huntress?
Huntress is a cybersecurity solution designed to detect and prevent threats and malware attacks within organizational IT environments. For more information about Huntress, visit https://www.huntress.com
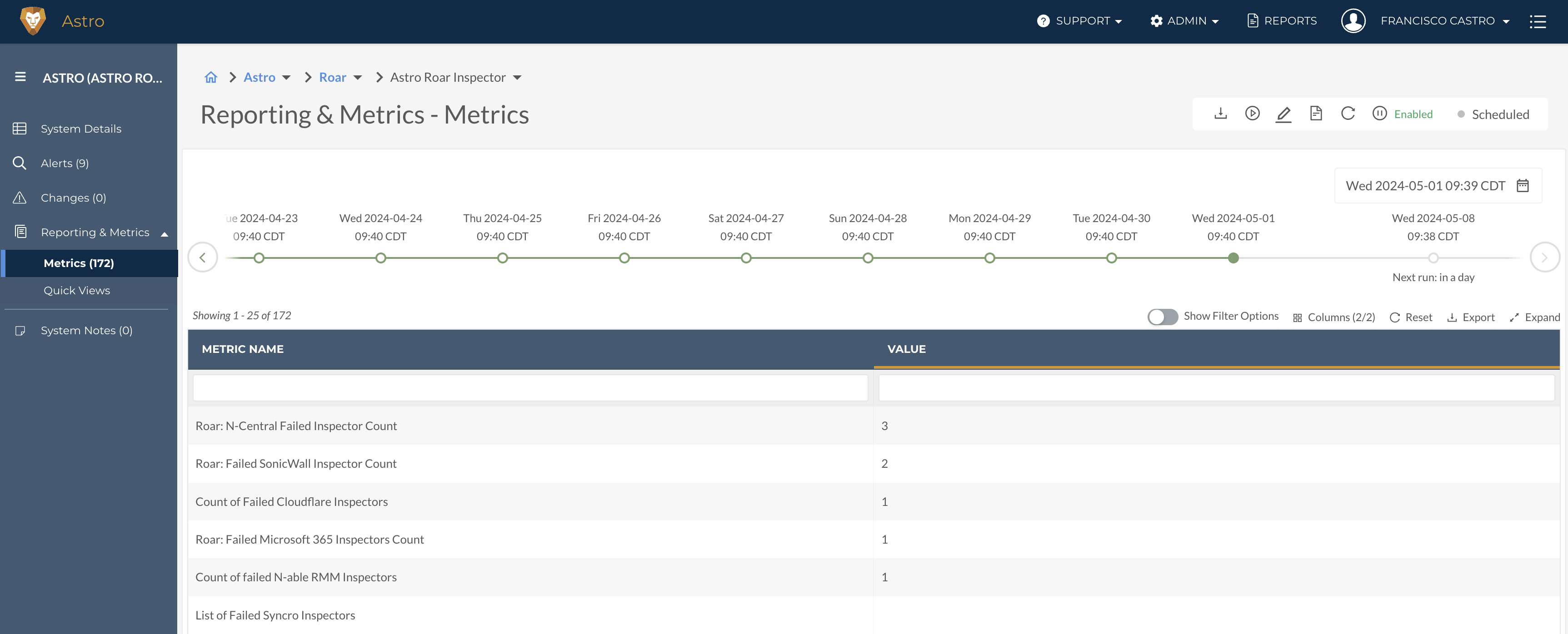
Roar Inspector is Now in Production with Newly Added Metrics
Liongard's Roar Inspector is now in official Production status, receiving several reliability and performance enhancements. As part of this update, we also added 145 metrics for the Roar inspector to help partners better manage failed inspectors and create alerts and reports to reflect failures that must be addressed.
The Roar Inspector allows for efficient management and oversight of your platform's performance by surfacing the status of your system inspectors and agents. With these new Metrics, creating Alerts for any Inspectors that require attention is easier than ever. Please visit our documentation for more information on the Roar Inspector and its configuration.
Microsoft 365 Inspector Configuration and Future Additional Data Update
Liongard has made modifications to the Microsoft 365 Inspector that will make previously missing data for Teams, OneDrive, and SharePoint in Microsoft 365 Child Inspectors accessible again in the upcoming June release. These data points include data print fields relating to SharePoint sites, OneDrive Drives, details on Teams applications, and more.
The modification to the Microsoft 365 Inspector includes newly added permission scopes that partners can configure today in preparation for the upcoming release when the new data will be available.
Please note that this step is ❗️optional❗️ and only required if you are interested in surfacing certain related data points related to mailboxes, OneDrive, Teams, and SharePoint within Microsoft 365 Child Inspectors.
❗️Optional Step❗️: Enabling Application Based PermissionsLiongard is an application that interacts many parts of Microsoft 365 to surface critical data points. In order to comply with Microsoft's granular delegated admin privileges and surface these newly available data points, partners must have the option of reconfiguring their GDAP relationships to include the
Privileged Role Administrator Entra ID security role.Once all relationships have been updated, navigate to the Liongard Microsoft 365 Inspector page. Open the Parent Inspector's configuration page and ensure that you have turned on the Enable Application Based Permissions toggle and its accompanying features:
Then, complete the “Sign-In” step and save the Inspector configuration.
For a more detailed explanation of the Entra application roles required by Liongard, please visit our Knowledge Base.
New Alerts Added to the Cyber Risk Alert Template
The Cyber Risk Alert Template has been updated with additional alerts to help mitigate cyber risks in your Environment. By proactively alerting you to potential threats to your user accounts, Firewalls, Domains, workstations, and more, these newly added alerts will enable you to stay ahead of evolving cyber threats and secure your attack surface.
Below is a list of the newly added alerts:
- Active Directory | User Accounts With Brute Force Attempts
- Active Directory | Privileged User with Stale Password
- Active Directory | Locked Out Users
- Azure Active Directory | Medium Level and At Risk User Identified
- Azure Active Directory | High Level and At Risk User Identified
- Cisco Meraki | Exposure to Wireless Network Due to Weak Encryption
- Cisco Meraki | Exposure to Network Due to Lack of Segmentation
- Cisco Meraki | Exposure to Wireless Network Without Pre-Shared Key
- Cisco Meraki | Potential Outage Due to Lack of License
- Google Workspace Inspector | MFA Not Enabled on Enforced Account
- Google Workspace Inspector | Privileges Added/Removed/Modified
- Internet Domain | Expiration
- Internet Domain | Email Forgery Exposure
- Internet Domain | DNS Poisoning Exposure
- Microsoft 365 | Users with Risk Policy Disabled
- Microsoft 365 | Exposure to User Account(s) Due to Lack of Strong Authentication
- Microsoft 365 | Exposure to Account(s) With Weak Password
- Microsoft 365 | Serious Exposure to Privileged Account(s) Due to Overuse
- Microsoft 365 | Exposure to Privileged Account(s) Due to Lack of Strong Authentication
- Microsoft 365 | Internal Forwarding Rule Added/Removed/Modified
- Microsoft 365 | External Forwarding Rule Added/Removed/Modified
- Microsoft 365 | Exposure to Suspicious Sign-Ins
- Sonicwall | HTTP User Login Allowed
- Sophos Central | Tamper Protection Is Disabled
- Sophos Central | Service Health not in Good State
- Sophos Central | Threat Health not in Good State
- Sophos Central | Endpoints not seen in the last 30 Days
- TLS/SSL | Web Traffic Exposure to Sniffing and Lack of Website Validation
- TLS/SSL | Serious Exposure to SSL Forgery / Interception
- TLS/SSL | Weak Protocol Supported
- TLS/SSL | Certificate Expiration
- Ubiquiti UniFi | Change to Member Devices
- Watchguard Inspector | Management User Locked Out
- Windows Server | RDP Enabled on Server
- Windows Workstation | Defender Threats
- Windows Workstation | RDP Enabled on Workstation
- macOS | Antivirus On System Changed
- macOS | Change to List of Local Users
- macOS | File Vault Encryption disabled
- macOS | Firewall disabled
- macOS | Firewall Stealth Mode disabled
- macOS | Remote Login enabled
- macOS | Remote Management enabled
- macOS | Remote Apple Events enabled
Minor Updates and Bug Fixes
Platform and Feature Minor Updates and Bug Fixes
- Fixed an issue where the system re-enabled change detections after a user disabled them
- Corrected the "Fortinet FortiGate: Firewall Policy Summary" metric so that
dstinfin the data-print is now labeled as ‘Destination Interface’ - New Agent Version 4.2.7. Upgraded the version of Node.js used by the Liongard Agent to mitigate several security vulnerabilities
Integration, and Inspector Minor Updates and Bug Fixes
- All Inspectors
- Fixed an issue where inspection logs were not being populated
- Autotask
- Autotask Inspector now allows downloads up to 50,000 contacts by increasing the limit from 10,000
- Identity Monitoring
- Resolved an issue that prevented the configuration page from opening
- Microsoft 365
- Fixed the Inaccurate Last login column in data-view report tables
- SonicWall
- Added support for SonicWall OSX 7 (NSv)
- Ubiquiti Unifi
- Enhanced the Unifi Ubiquiti Inspector to provide clear error messages
New Liongard for Account Managers Learning Path in Liongard Academy
Liongard Academy, our learning and resource center, has just released a new Liongard for Account Managers certification learning path.
This learning path is designed for Account Managers and vCIOs seeking to deepen their understanding and proficiency with Liongard's Attack Surface Management. It includes courses covering fundamental knowledge of Liongard's platform and practices for leveraging Liongard for effective risk management, compliance, and customer relationship enhancement.
By completing this certification, Account Managers at MSPs will be equipped to effectively use Liongard to support their roles, drive customer success, and enhance their strategic decision-making processes.
This learning path is composed of 4 essential courses:
-
Introduction to Liongard: Acquire a thorough understanding of Liongard's platform, main features, and functionalities.
-
Cyber Risk Essentials: Understand the basics of cybersecurity risks and how Liongard can help mitigate these risks.
-
Improving Customer Relationships with Liongard: Learn how to use Liongard’s insights and reports to strengthen customer relationships.
-
Get to Data Faster with Metrics and Reports: Become proficient in using Liongard’s reporting and metrics tools for efficient data access and analysis.
Check out our other coursework, including "Troubleshoot Customer Issues faster" and "How to Write a Metric Learning Path." Check out our Team Training documentation for more information on role-specific training.
Sign up today at Liongard Academy.
As always, feel free to share any feedback or questions in the Liongard Lounge, our Slack community, in the #liongard-academy channel!
Liongard Library
Have you checked out the Liongard Library yet? Share custom Metrics and learn best practices from other Partners to get the most out of the platform. Access it in the Support drop-down menu in your instance.
Visit the Liongard Library today!
Updated 5 months ago

