Using Liongard's Prebuilt Actionable Alert Templates
Liongard's Prebuilt Templates
In all Liongard instances, there are a number of prebuilt templates that are meant to give you a starting point for using Liongard's Actionable Alerts.
With these prebuilt templates, you can apply alerts across multiple inspectors per environment, helping you flag common cross-inspector issues, streamline billing, and escalate issues to support with ease.
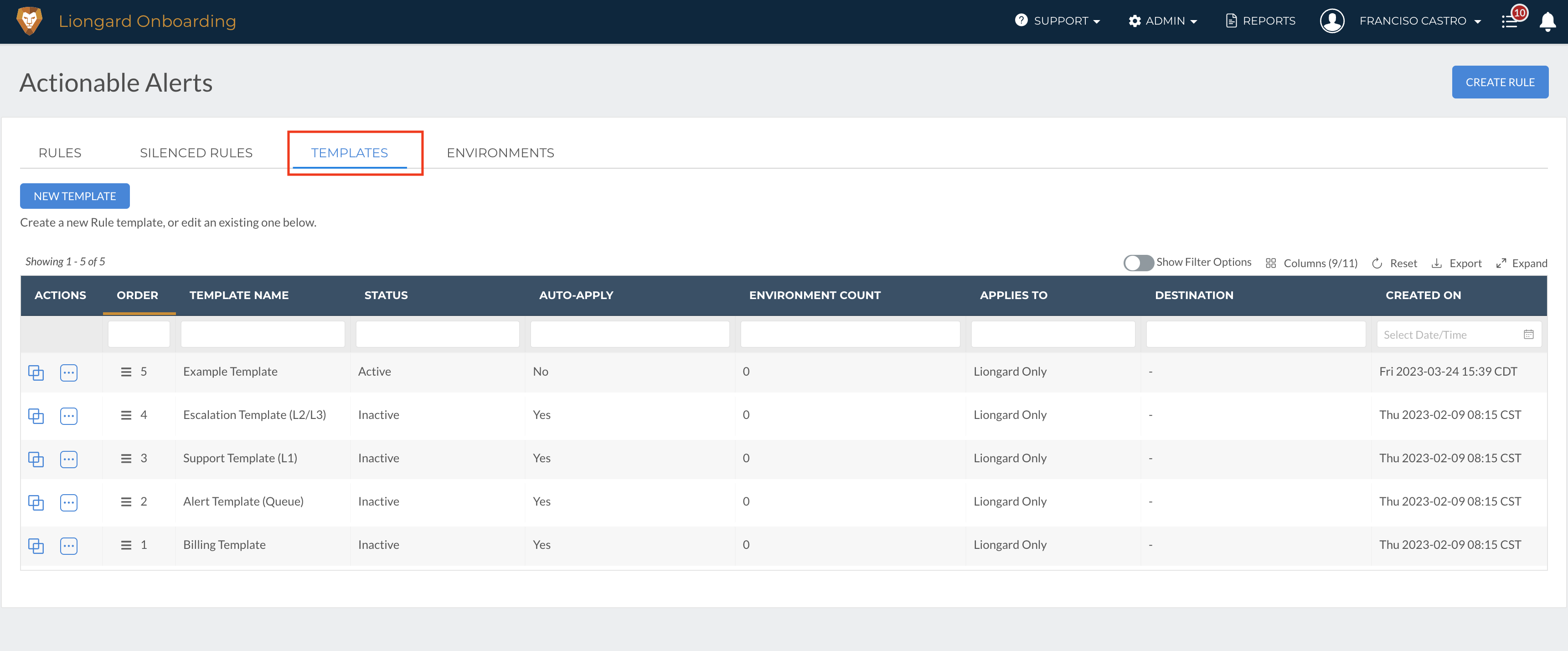
Alongside these use-case templates, we also have an "Example Template." Within this template, there are seven high-value Actionable Alert rules enabled.
Rules enabled in the Example Template:
- Active Directory | Change to Privileged Users
- Active Directory | Privileged User with Stale Password
- Internet Domain | Expiration
- Internet Domain | Change to MX Record
- Microsoft 365 | Change to Privileged Users
- TLS/SSL | Certificate Expiration
- Windows Inspector | Local Privileged User Added/Deleted
This template is automatically activated in your platform and set to open alerts in Liongard only. The template is auto-applied to all Environments, so once you import companies/customers into Liongard and activate Inspectors, this template is live, and it will trigger alerts in Liongard.
Liongard's Example Template is meant to be a starting point for using Liongard's Actionable Alerts. We recommend editing this template to best meet you and your team's needs. This includes removing and adding new rules to the template and setting it to send alerts to your PSA/Ticketing System or Email(s).
Best Practice: Example Template Alert Fine Tuning
Overview
In order to avoid flooding your service board/ticket queue/email with tickets that you may or may not find valuable, we have developed this best practice for fine tuning Actionable Alerts.
The purpose of this best practice is to identify the highest value rules for your IT Service Provider and to complete an audit of what alerts Liongard can capture on the systems you're managing using Liongard's Example Template as a starting point.
Step 1: Review Open Alerts in Dashboard
Because Liongard's Example Template is activated by default, once you import companies and roll out Inspectors, Actionable Alerts will trigger once the criteria of a rule are met.
Liongard recommends you review any alerts that have been triggered, navigate to your Dashboard > Total Open Alerts tab. Here, you will see any open alerts across all Environments in Liongard.
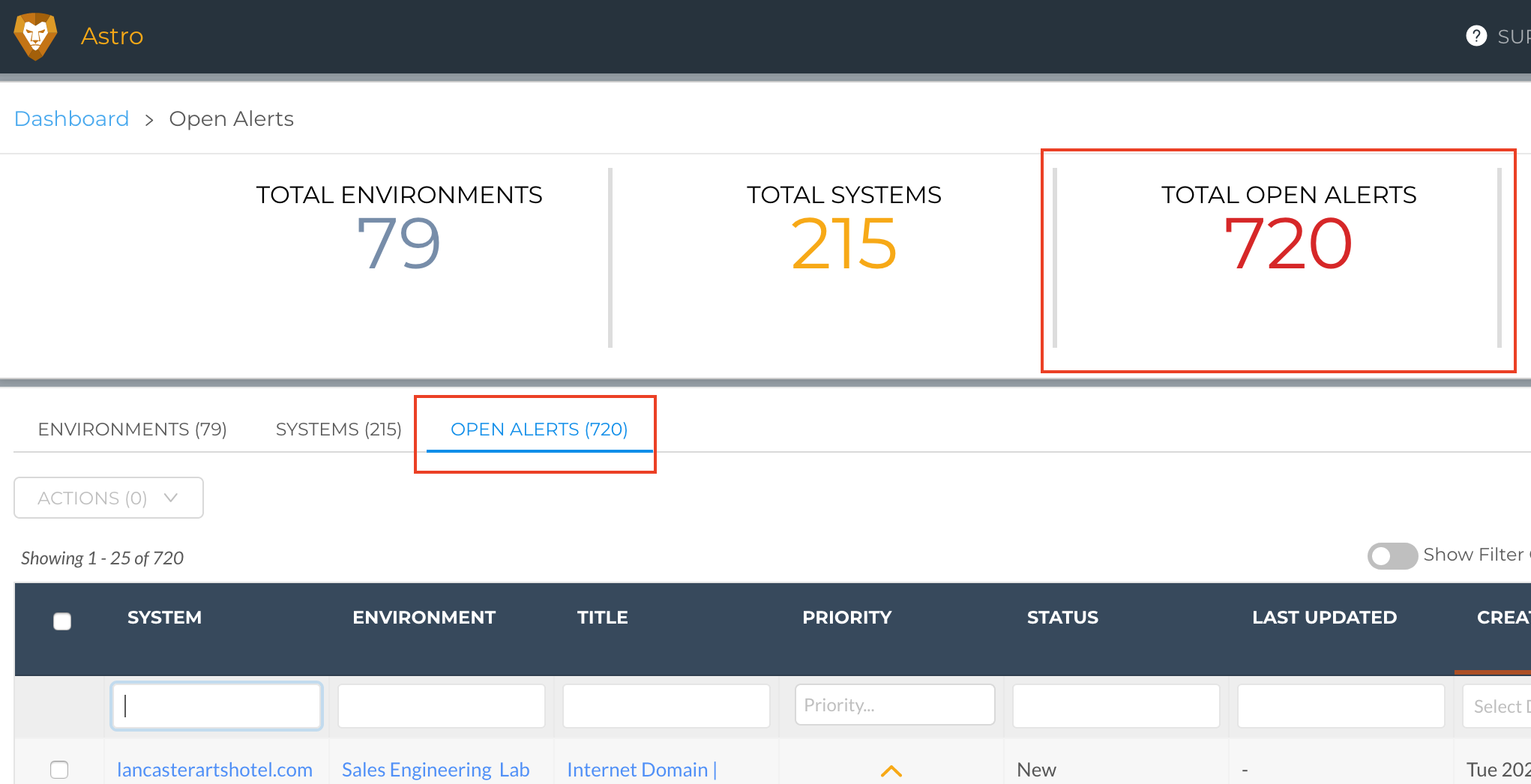
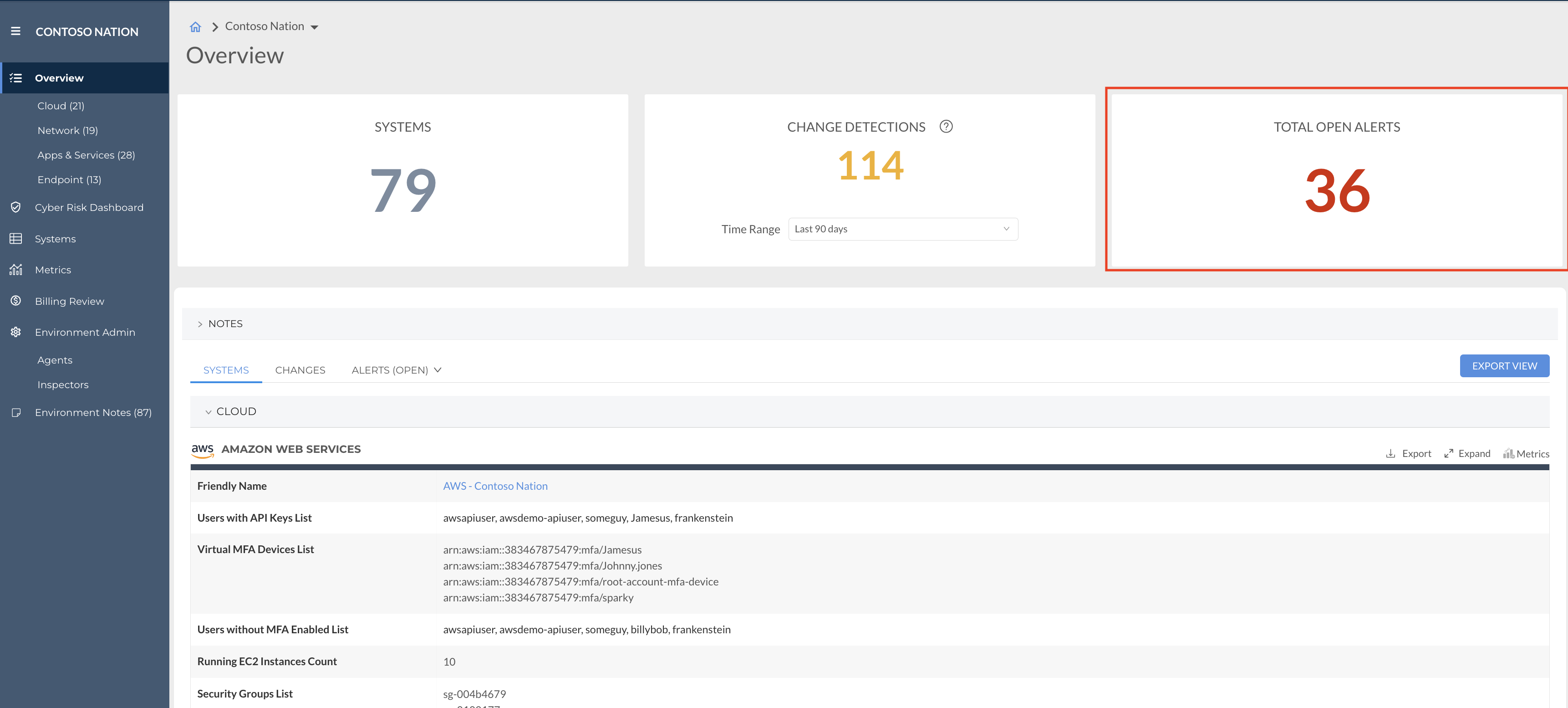
You can also see alerts by Environment by navigating to your Dashboard > Environments tab > Clicking into an Environment > Total Alerts. Here, you can review any alerts, open or closed, for this Environment.
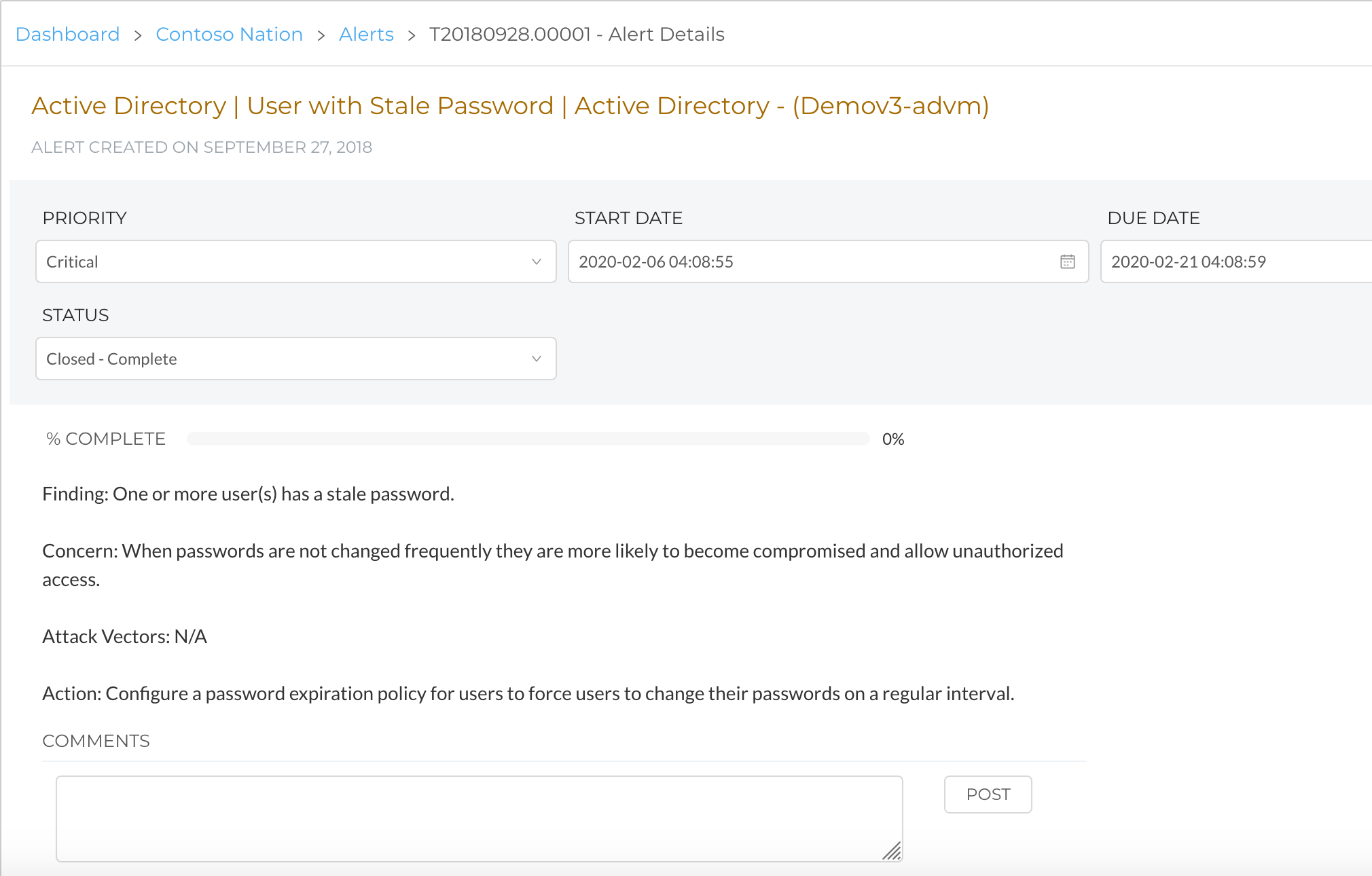
To review an alert, click into the Title. For more information on reading Actionable Alerts, review our documentation.
Step 2: Review and Scope Liongard's Example Template
Now that you have reviewed open alerts, it is time to determine which rules are most relevant to you and your team by reviewing and scoping Liongard's Example Template.
To do so, navigate to Admin > Actionable Alerts > Templates > Select the three dots next to Example Template > Select Edit the Template
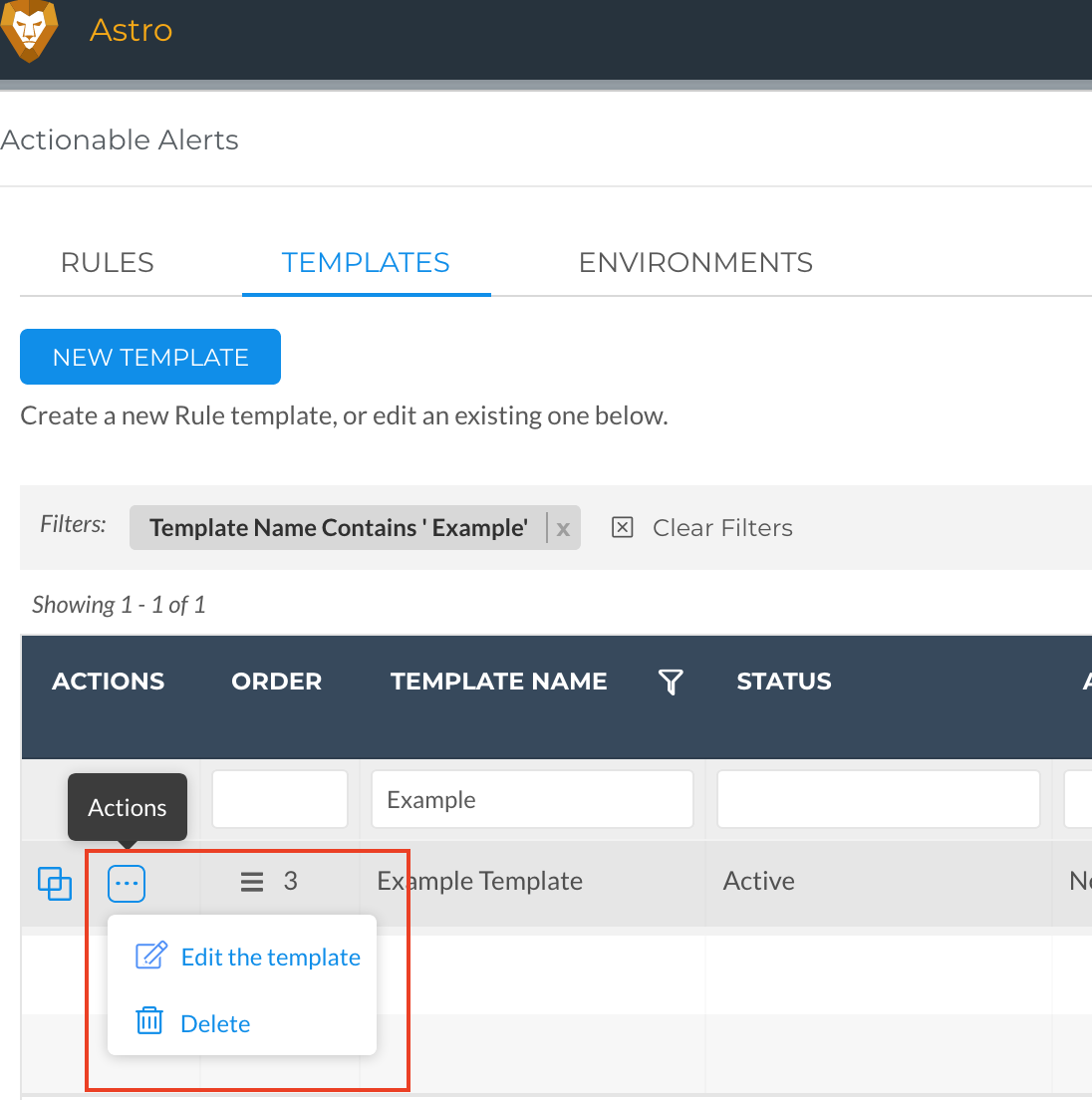
At the bottom of the screen, you will find a table of Liongard's Actionable Alert rules. By default, there are seven rules already enabled. To review what rules are enabled in the Example Template, filter by the Enabled column.
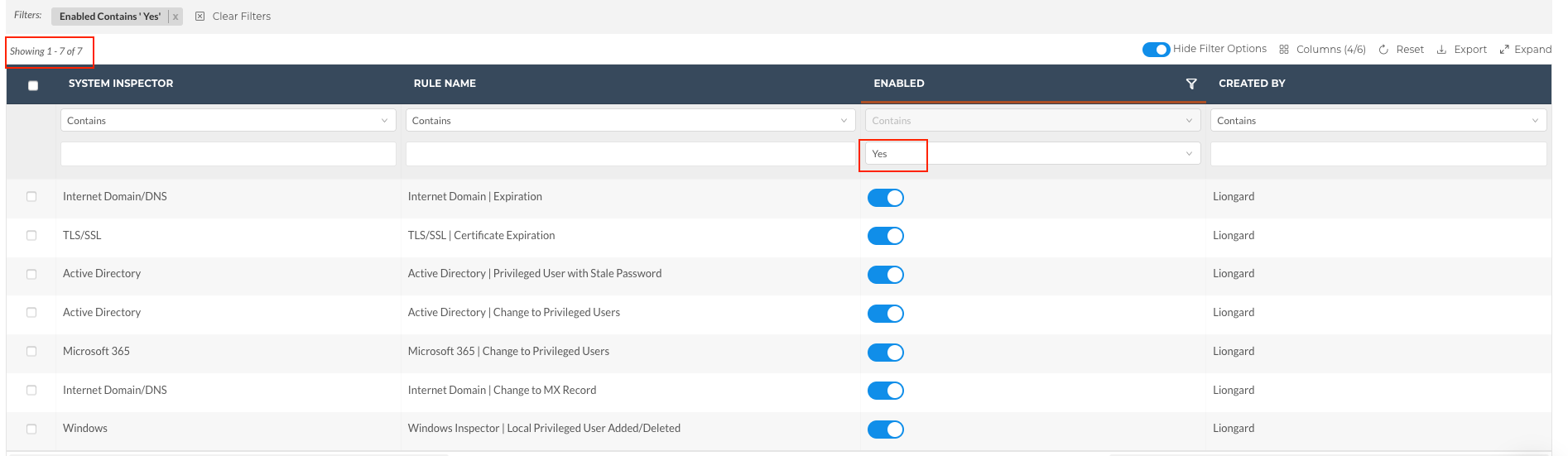
Then, review and determine whether the rules enabled are valuable for your team. To disable a rule, you can either toggle off the Enable toggle for individual rules, or you can bulk select rules and disable them n the Actions menu.
Additionally, you may see additional rules that you would like to enable. To turn on a rule that is not enabled in the template, you can either toggle on the Enable toggle, or you can bulk select rules and enable them in the Actions menu.
You also have the ability to edit and customize any of Liongard's existing rules as well as the ability to write your own custom Actionable Alerts. Please visit our How to Write a Custom Actionable Alert documentation to learn more.
New Rules and Updating TemplatesWe recommend reviewing Liongard's Actionable Alert rules Library and updating your existing templates monthly. To do so, navigate to Admin > Actionable Alerts > Rules tab.
Any rules added within the past 30 days will be highlighted in green.
When you click into edit a template, new rules added to the Library will also be displayed. You can then enable these rules in existing templates or add them to any new template.
Step 3: Actionable Alert Audit
Now that you have reviewed and scoped your Example Template. We recommend allowing all your Inspectors to run for at least 24 hours so you have an idea of what alerts will trigger.
As noted above, once inspections complete, you will find alerts triggered in Liongard in the Dashboard screen as well as in an Environment's Single Environment Dashboard. Just as above, we recommend reviewing the alerts triggered.
Step 4: Edit Example Template and Assign Template to PSA/Email Integration
Pre-work: Set up your PSA (Ticketing System) or Email IntegrationIf you would like Liongard to send tickets to your PSA, Microsoft Teams, or email(s), you must complete a basic integration of Liongard to your PSA, Microsoft Teams, or email(s).
Follow the instructions below to get started with these integrations:
After allowing all Inspectors to run (usually within 24 hours), it's now time to continue editing your Example Template.
While reviewing your triggered alerts, ask yourself, "Can I imagine this alert in my service board/ticket queue or email inboxes?"
- If the answer is yes, great! That alert rule is already turned on in your Example Template.
- If the answer is no, also, great! Navigate to Admin > Actionable Alerts > Templates > Select the three dots next to the Example Template > Edit the Template > Find the rule that you would NOT like to push to your PSA or Email inboxes and toggle off the Enabled toggle.
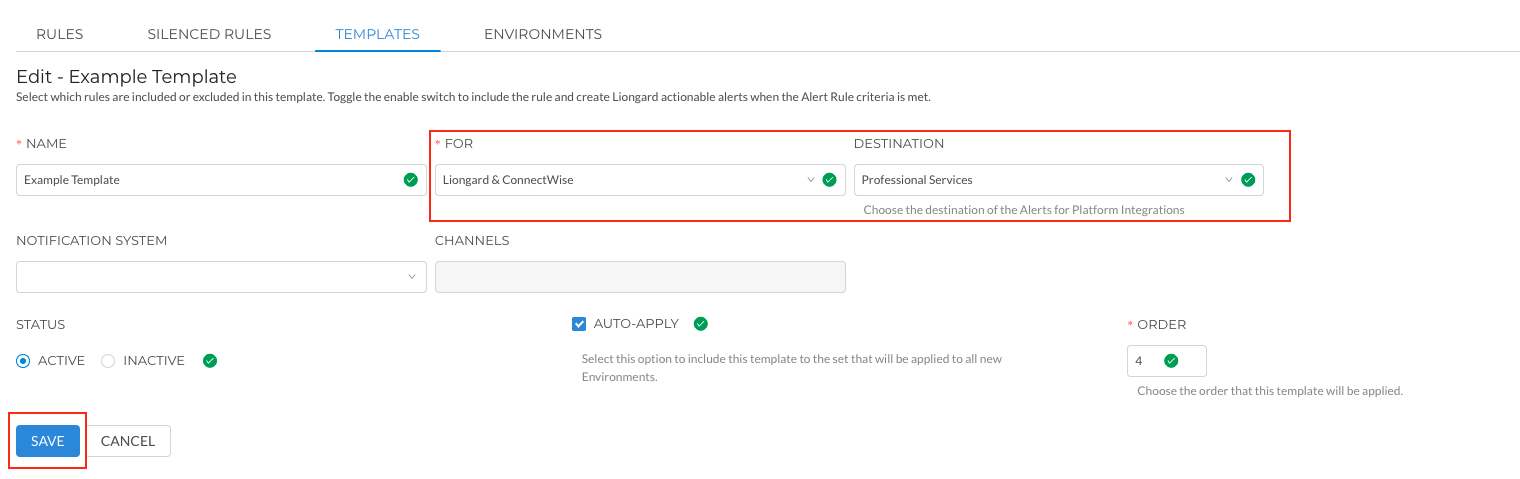
After you have scoped your Example Template down to include only the rules that you would like in your PSA/Email inboxes, you can then change the For field to be set to Liongard and your PSA/Email(s), and select the Destination where you would like the alerts to land.
Optionally, using the Notification System field, you can choose to send Actionable Alerts as notifications to Microsoft Teams. Once Microsoft Teams is selected, you can then select the desired Channel(s) to receive Actionable Alerts.
Lastly, select Save.
After your Inspectors complete their next inspection, they will push any triggered alerts as tickets to your PSA or Email inbox(es) as well as create alerts in Liongard.
Step 5: Continue Building Templates
Depending on your team's needs, you may want to create additional templates. Follow our steps for How to Set up Actionable Alerts.
Additional High-Value Rules
Partners frequently ask us what rules we recommend they enable in their templates; however, because every IT Service Provider does business differently, this can be challenging to recommend.
With that, here is a list of rules Liongard believes to be high-value:
- Active Directory | Never Used User Accounts
- Active Directory | User Accounts With Incorrect Passwords
- Active Directory | User Accounts With Brute Force Attempts
- Active Directory | Default Guest Account Enabled
- Active Directory | Domain Mode at or near End of Support
- Active Directory | Forest Mode at or near End of Support
- Active Directory | Servers at or near End of Support
- Active Directory | Default Domain Policy - Minimum Password Length Too Short
- Active Directory | Default Domain Policy - Password Complexity Not Activated
- Active Directory | Default Domain Policy - Account Lockout Threshold Not Set
- Active Directory | Recycle Bin Not Enabled
- Amazon Web Services | Auditing and Logging Not Activated
- Amazon Web Services | Exposure to Accounts Due to Lack of Strong Authentication
- Cisco ASA | Change to Software Version
- Cisco ASA | Change to Configuration
- Cisco IOS | Change to Software Version
- Cisco IOS | Change to Configuration
- Cisco Meraki | Potential for Outage if License Not Renewed
- Cisco Meraki | Potential Outage Due to Lack of License
- Continuum RMM | Failed or Stale Agents
- Datto | A Recent Backup Has Failed
- Datto | A Datto Backup Has Not Completed in the Last 24 Hours
- Datto BCDR | Local Disk Usage
- Fortinet | Change to Software Version
- Hyper-V | Unhealthy Storage Volume(s)
- Internet Domain | Email Forgery Exposure
- Internet Domain | Email Forgery Exposure Due to Lack of DKIM Usage
- Internet Domain | Email Forgery Exposure from Rogue Source
- Internet Domain | Change to NS Record
- Microsoft 365 | Exposure to Privileged Account(s) Due to Lack of Strong Authentication
- Microsoft 365 | Serious Exposure to Privileged Account(s) Due to Overuse
- Microsoft 365 | Multiple Unassigned Microsoft 365 Licenses
- Microsoft 365 | Exposure to User Account(s) Due to Lack of Strong Authentication
- Microsoft 365 | Exposure to Suspicious Sign-Ins
- Microsoft 365 | User Risk Policy Disabled
- Microsoft 365 | Exposure to Stale or Disused User Accounts
- pfSense | Change to Software Version
- Sonicwall | Potential for Outage App If Signature DB Expires
- Sonicwall | HTTP User Login Allowed
- Sonicwall | Potential for Outage If License Expires
- Sonicwall | Device Restart Required
- SonicWall | NAT Rule Contains Phrase 'Terminal Services'
- SQL Server | Scheduled Maintenance Plan Has Not Run
- SQL Server | Database in Offline State
- SQL Server | Database in Restoring State
- SQL Server | Database in Recovering State
- SQL Server | Database in Recovery Pending State
- SQL Server | Database in Suspect State
- SQL Server | Database in Emergency State
- SQL Server | Database in Read Only Mode
- SQL Server | Master System Database with No Recent Backup
- SQL Server | MSDB System Database with No Recent Backup
- SQL Server | Model System Database with No Recent Backup
- SQL Server | Database with No Recent Backup
- SQL Server | Database with Full Recovery Model and No Log Backups
- SQL Server | Change to Privileged Users
- SQL Server | Change to Software Version
- TLS/SSL | Weak Protocol Supported
- TLS/SSL | Auto-Renewing Certificate Expiration
- VMware ESXi | License Expires within 30 days
- VMware ESXi | Software Serial Number Modified
- VMware ESXi | Host NICs Not Negotiated At Full Duplex
Updated 5 months ago
