Release Notes Through 2020-06-08
Platform Updates
Export Single System Inspector Data
You can now export Single System Inspector data from Liongard to Excel.
The Excel export will include an overview sheet with an additional sheet for each Data View tab.
Deprecating TLS 1.0 and 1.1 Protocols
In our next release, scheduled for June 24, 2020, we will deprecate the TLS 1.0 and 1.1 protocols from the Liongard application itself.
All browsers used for Liongard and tools interacting with our API will need to support at least TLS 1.2.
Below are browsers known to not support at least TLS 1.2 include:
- Android 4.3 and earlier versions
- Firefox version 5.0 and earlier versions
- Internet Explorer 8–10 on Windows 7 and earlier versions
- Internet Explorer 10 on Windows Phone 8.0
- Safari 6.0.4/OS X 10.8.4 and earlier versions
Feature Updates
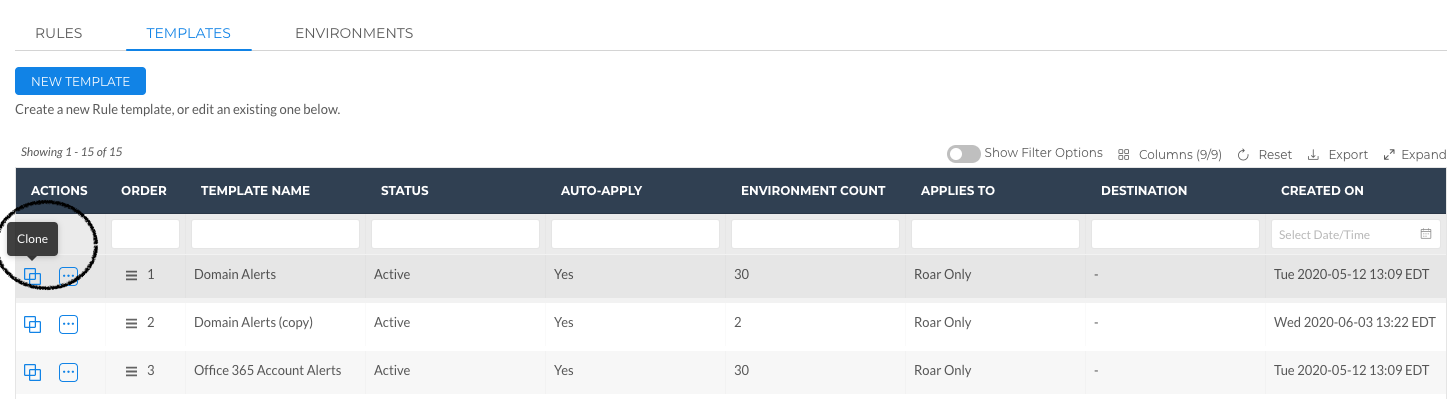
Clone Actionable Alert Templates
Users can now clone Actionable Alert templates. To learn more, please review our documentation on how to Clone an Existing Template.
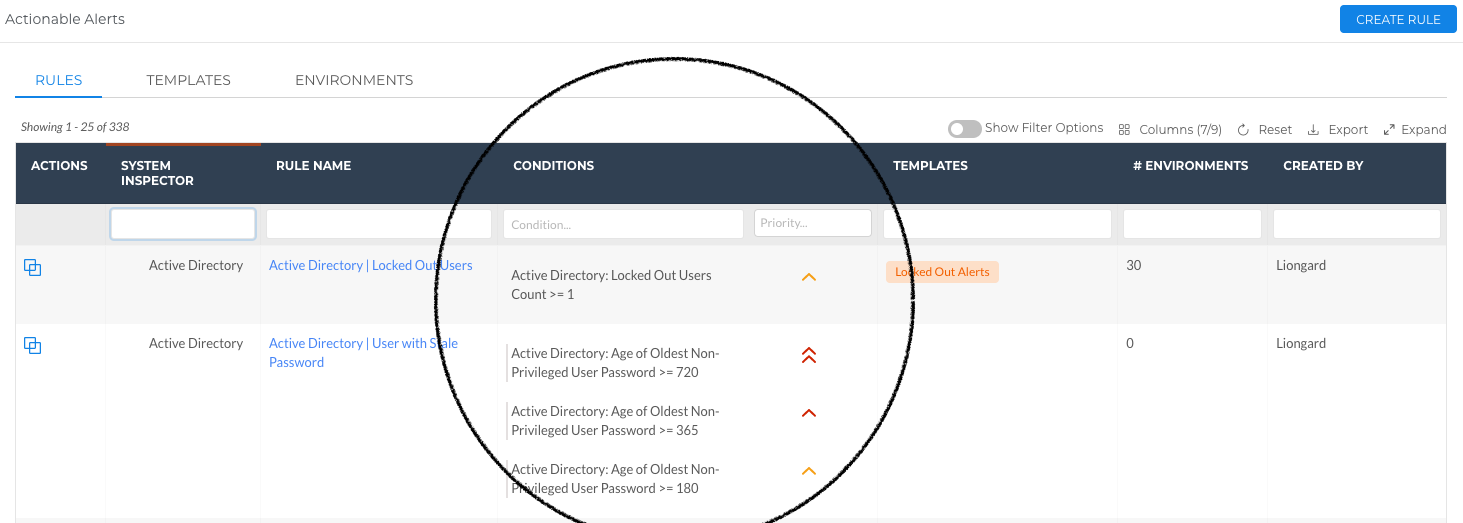
Conditions and Priority Columns added to Rules Library
A column for rule conditions and priorities now exists in the Rules Library. This will allow users to view and filter rule conditions and priorities in one place.
Inspector Updates
Azure Active Directory Inspector
- Added platform mapping for IT Glue and ConnectWise
- Updated error log messages for calls to the Graph API that fail due to missing API scopes
- Added graceful handling for Intune license-dependent endpoints which make it possible to inspect a tenant that lacks an active license
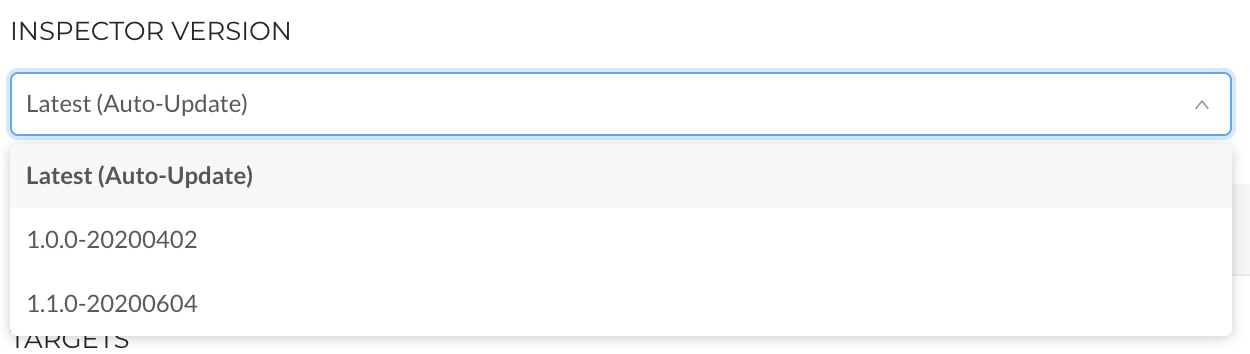
Update to Network Discovery Inspector in Beta Stage
Currently, our team is building more capabilities into our Network Discovery Inspector. To test our most recent beta version, you can change your Network Discovery Inspector's Version to 1.1.0-20200604 in your Inspector's configuration details.
To test the beta version of the Inspector, please review our documentation.
Improvements include:
- Improved the Network Discovery Inspector's host discovery algorithm to more effectively discover hosts on the network.
- Updated the Network Discovery Inspector's input to allow for IP ranges in any size subnet, not just /24 networks. Also, updated the input format to make it easier to input ranges.
IT Glue Inspector
- The IT Glue Inspector now auto-discovers Internet Domain Inspectors from domains in IT Glue
- Removed some unnecessary calls to the IT Glue API
- Improved Inspector logging
Office 365
- Improved performance and reliability of the Office 365 Inspector by removing a call to retrieve message rules for Office 365 users that are not mail-enabled
- Modified a number of Office 365 Metrics to reliably return integers for cleaner display in Liongard and BrightGauge
- Updated the “Office 365: Assigned License Summary” Metric to be easier to read
Bug Fixes and Minor Updates
- Improved messaging under Status Details for failed ConnectWise and IT Glue Mappings
- Updated terminology in the rule builder from "Launchpoint" to "System"
- Updated a bug for the GoDaddy Inspector that was driving unnecessary API usage and inspection failures
- Removed a hashed secret value from the SonicWall Inspector Data Print
- Improved performance and reliability of the Liongard Inspector by scoping down calls to retrieve timeline entries from Discovered Systems
- Addressed an issue for the Cisco ASA Inspector in which the parsed running configuration was not being included in inspection payloads
- Modified several Metric queries in our default library of Metrics to be more concise and return more reliably
- Corrected misspellings in several Active Directory Actionable Alert rules
- Updated an erroneously named Metric for the WatchGuard Inspector
- Updated the Auvik Inspector template, so users can use the cluster name
- Corrected an issue that could cause the Metric query for the Datto BCDR Inspector to return a null value, resulting in failure to evaluate a rule
- Added data to the Active Directory Inspector that indicates when there is a “loop” in Active Directory group nesting
Updated about 2 months ago
