Active Directory Inspector KB and FAQs
How is the "Security Score" for users constructed?
The security score is based on the following security settings per user:
- Is a password required for the user?
- Is the password non-reversible?
- Does the password expire?
- Is the password changeable?
- Does the user get locked out after five or less bad password attempts?
- Are passwords required to be at least 10 characters long?
- Is there a password complexity requirement in place?
Each "yes" response is weighted evenly, so if you have 6/7 requirements, your security score would be 85.7.
How are the "User Activity" and "Computer Activity" values determined?
The statuses are determined as follows:
New & Never Used:
- Enabled
- Created less than seven days ago
- Never logged on
Never Used:
- Enabled
- Created more than seven days ago
- Never logged on
In Use Recently:
- Enabled
- Logged in within the last 30 days
Stale:
- Enabled
- Last login was more than 30 days ago
How are group changes over the last 24 hours determined?
Liongard looks at replication logs over the last 24 hours where attribute metadata replication has occurred on any of the protected groups (detailed above). It looks for any linked objects, in this case Groups or Users. It does not pull the actual metadata changes only linked object changes.
It depends on SDAdminHolder propagation sync setting. This is normally set to 60 minutes, but it can be adjusted by editing your registry setting.
To edit the sync time, use the following command:
REG ADD HKLM\SYSTEM\CurrentControlSet\Services\NTDS\Parameters /V AdminSDProtectFrequency /T REG_DWORD /F /D 600 (600 = number of seconds)
Can I exclude users from User-Related Active Directory Actionable Alerts?
For several Active Directory User-Related Actionable Alert Rules, built-in is an if statement, stating that if a user is in a group called “RoarExclude” then exclude them from this Alert. To utilize this feature, you will need to create a Security Group named “RoarExclude”
The following Metrics include the RoarExclude filter and can be used for custom Actionable Alert Rules:
- Active Directory: End of Life Workstations (Excludes Roar Group)
- Active Directory: Age of Oldest Privileged User Password
- Active Directory: Privileged Users with Stale Password List
- Active Directory: Age of Oldest Non-Privileged User Password
- Active Directory: Non-Privileged Users with Stale Password List
The following prebuilt Actionable Alerts include the RoarExclude filter:
- Active Directory | Privileged User with Stale Password
- Active Directory | User with Stale Password
To exclude a user from another Active Directory Metric, at the Users object level, inside the brackets, add the condition followed by the exclusion string as shown here:
Users[?first condition && !contains(MemberOfStr, `RoarExclude`)]What is a Detached Group Policy?
A Detached Group Policy refers to a Windows Group Policy that is not associated with a specific OU.
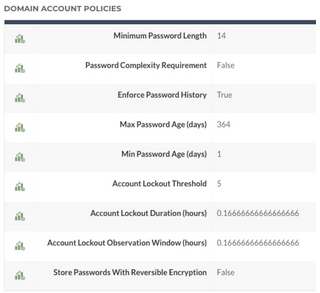
Where is the Domain Account Policy data pulled from on the Overview Page?
Typically, the information found in the Domain Account Policies section of the Overview page is being pulled from the Default Domain policy.
Why does my Active Directory Inspector return blank DHCP data?
The Active Directory Inspector will only return DHCP details when deployed to the machine running the DHCP role.
Updated 6 months ago
