Updating Microsoft Cloud Service Inspectors for Granular Delegated Admin Privileges
Overview
Liongard has released an update to our Microsoft Cloud Inspectors to make sure they’re ready for Microsoft’s upcoming transition from Delegated Admin Privileges (DAP) to Granular Delegated Admin Privileges (GDAP).
Partners will need to update their Parent Microsoft Cloud Inspectors for them to continue working properly using the configuration steps listed below.
Prerequisites
If you have a current Microsoft Parent inspector that is tied to a Microsoft account you use to manage customer relationships via the Microsoft Partner Center, then you will use the Multi-Tenant setup steps.
Before you can update your Multi-Tenant Microsoft Cloud Parent Inspectors in Liongard, ensure that you have successfully transitioned your customers' tenant to GDAP. In order to proceed, please note that you will need to login to your Microsoft Partner Center with a user that is assigned the Admin Agents role.
For more information, please watch [this video](Liongard has recently updated our Microsoft Cloud Inspectors for the upcoming Microsoft GDAP changes. Watch the full video to ensure that your GDAP is correctly set up to work with this new Inspector. Once you are finished, watch the following video to complete the necessary steps in Liongard. For more information on GDAP, please visit Microsoft's documentation: https://learn.microsoft.com/en-us/partner-center/gdap-introduction) for a detailed walkthrough of this process or visit Microsoft's documentation. Additionally, please verify the account used with your parent inspector is a member of the "AdminAgents" group in your parent Azure Active Directory tenant.
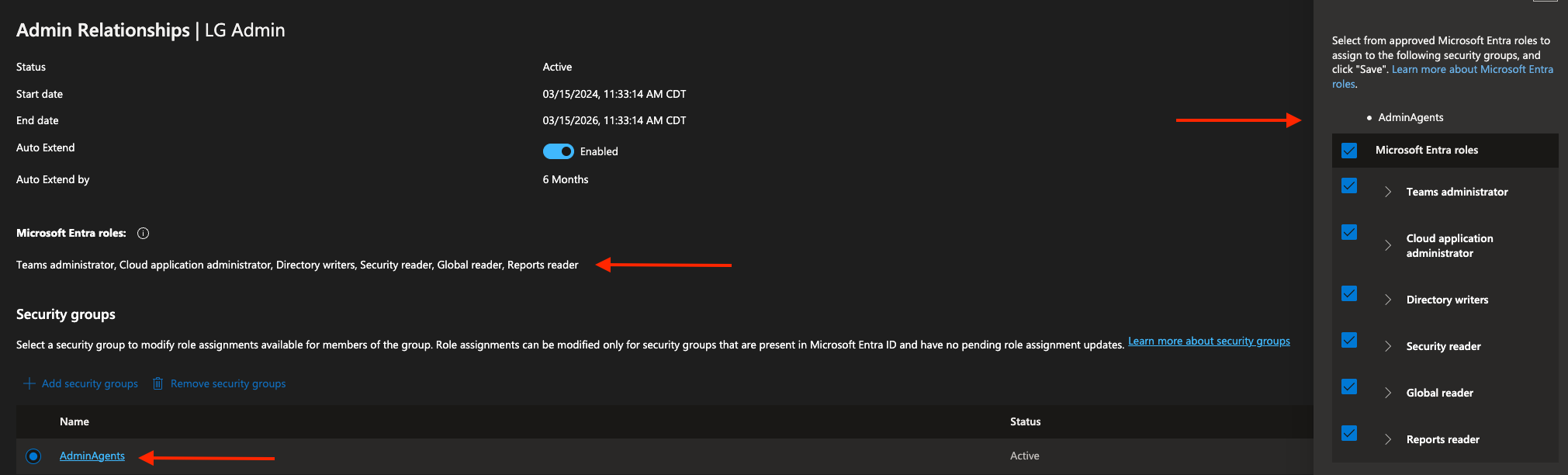
In order to validate that your Child Inspectors are ready for Liongard's update, within the Microsoft Partner Center ensure that your customers' GDAP relationship has the Teams Administrator, Cloud application administrator, Directory writers, Global reader, Security Reader, and Reports reader Azure AD roles applied in addition to the AdminAgents security group assigned with the 6 Azure AD roles for that admin relationship, as shown below.
Frequently Asked Questions
What permissions does the user within Microsoft need to have to update the Parent Inspectors' authentications?The user will need to be assigned Application Administrator, Global Reader, Reports Reader, and Security Reader, and Teams Administrator Azure AD roles for the tenant associated with the Parent Inspector in addition to being assigned to the Admin Agents role within the Partner Center.
It is possible to setup the GDAP relationships required for the Multi-Tenant setup in bulk?Yes! Microsoft provides a bulk-migration tool which you can find here. We would also recommend CyberDrain's CIPP tool as a more user-friendly alternative. Please note, if using the bulk method you will still need to follow our guidance on how to setup the GDAP relationships per the prerequisite section above.
Here is a helpful video that goes over the setup steps and difference between the two bulk-migrations tools.
How does this transition impact data returned by Liongard's Microsoft Cloud Parent Inspectors?As it currently stands, some of the Microsoft Graph API endpoints have not been updated to support GDAP. Because of this, some of the data previously returned by Liongard's SharePoint, OneDrive, and Teams Child Inspectors will be impacted until Microsoft updates the Microsoft Graph API. Scroll down or click here for a detailed list.
Configuration Steps
Parent Inspectors
The following steps are only necessary for any existing Microsoft Cloud Service Parent Inspectors. All Child Inspectors will inherit the permissions.
Step 1: Reconfigure Parent Inspectors
Depending on the relationship to the tenant(s) that you manage, your configuration steps will be different. Microsoft Cloud Service Inspectors in Liongard will fall under one of two categories: Multi-Tenant or Single-Tenant configurations.
| Setup | Description |
|---|---|
| Multi-Tenant | I have a Microsoft account I use to manage my customer relationships via the Microsoft Partner Center. |
| Single-Tenant | I have a Microsoft account that I access directly to manage my customer on their behalf. I do not manage this customer in the Microsoft Partner Center |
If this is a Multi-Tenant setup, ensure that you have completed the prerequisite steps as outline above.
Identify the legacy Microsoft Cloud Parent Inspectors and edit the Inspector(s).
In Liongard, navigate to Admin > Inspectors > Inspector Types > Navigate to the Appropriate Microsoft Inspector > Select the Inspector > Navigate to the Appropriate Parent Inspector > Select the Actions button > Select Edit.
Scroll down to the System Setting section:
- Find the Enable Multi-Tenant Application toggle. Leave the toggle on if you are setting up a Multi-Tenant Parent Inspector. Turn the the toggle off if you are setting up a Single-Tenant Parent Inspector.
- Select the "Open Microsoft Sign-In" button
- Authenticate with either of the following credentials, depending on your tenant relationship:
- Multi-Tenant: Sign-in the organization for the associated Tenant ID with an account that is assigned the Teams Administrator, Cloud Application Administrator, Global Reader, Reports Reader, Security Reader, and Directory Writer roles for Azure AD as well the Admin Agents role within the Partner Center.
- Single-Tenant: Sign-In into the organization for the associated Tenant ID with an account that is assigned the Teams Administrator, Cloud Application Administrator, Global Reader, Reports Reader, Security Reader, and Directory Writer roles for Azure AD.
- For both relationships, you may also sign-in into the organization with a custom Security Group, as long as the group is assigned the Teams Administrator, Cloud application administrator, Directory writers, Global reader, Security Reader, and Reports reader roles.
- Follow the prompts to accept the requested permissions by selecting checkbox to consent and select Accept
- A green check will appear to validate you successfully completed the step.
- ❗️Note❗️For the Multi-Tenant method, signing in with a user that has legacy MFA methods will result in Child Inspectors not being discovered. Please see this KB for more details.
- Select Save. The Inspector will now be triggered to run within the minute.
Microsoft Sign-In
You will need to sign in to for each additional Microsoft Cloud Parent Inspector you set up by signing in with the same account. However, you will not be prompted for the permissions consent.
Step 2: Repeat the Process for all Microsoft Cloud Parent Inspectors
For any other Parent Inspectors for the same tenant, repeat the Microsoft Sign-In process in the Inspector configuration page.
Bulk Schedule to Space Out Child Inspectors
Liongard recommends to space the Child Inspectors for the Microsoft Cloud Inspectors in order to prevent potential API throttling. To resolve this, follow these steps:
- Select All Child Launchpoints
Click the check mark box to select all child launchpoints in the bottom Inspector section
Click "Actions" > "Set Inspector Schedule"- Set Times to Space Out Launchpoints
In the screen on the right, select the checkbox for "Space These Launchpoints"
Set the interval to "5" and units to "minute(s)"- Select Save
Step 3 (Optional): Remove Previous Application
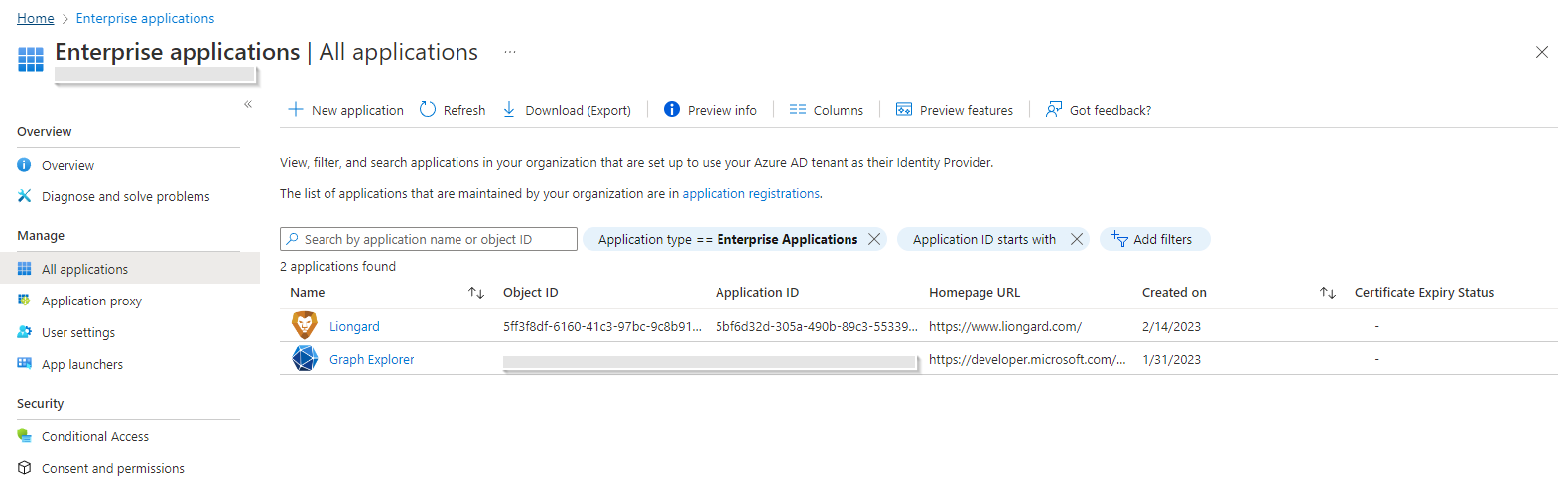
The previous Microsoft 365 Inspector configuration required you to create an application within your Azure Active Directory Tenant. You may remove this application from the "Enterprise Applications" section in the associated Azure Directory Tenant.
Removing Previous Application
The new configuration steps automatically creates a new application named "Liongard" with the current date in the Created On column. Be sure to refer to the Created On column to ensure you delete the previous application.
Inspector Data Points Impacted
Microsoft is continuing to update their Microsoft Graph API endpoints to support GDAP. As it currently stands, some of the Microsoft Graph API endpoints have not been updated. Because of this, some data previously returned by Liongard's SharePoint, OneDrive, and Teams Child Inspectors will be impacted until Microsoft updates the Microsoft Graph API.
Data Points No Longer Returned to Liongard After You've Updated Your Cloud Inspectors
365 Inspector
- Data Print Fields: MailRules, Users[].userPurpose
- Metrics: Office 365: Internal Forwarding Rule Summary, Office 365: External Forwarding Rule Summary, Office 365: Mailbox Rules Count, Office 365: Mailbox Rules with Errors List, Office 365: Mailbox Rules with Errors Count
- Actionable Alerts: Microsoft 365 | External Forwarding Rule Added/Removed/Modified, Microsoft 365 | InternalForwarding Rule Added/Removed/Modified
- Integration Mappings: N/A
SharePoint Inspector:
- Data Print Fields: Sites, Drivers, Lists, Pages
- Metrics: All metrics are still in the platform but will only be available for parent SharePoint Inspectors.
- Actionable Alerts: N/A
- Integration Mappings: N/A
OneDrive Inspector:
- Data Print Fields: SystemInfo.UserDriveCount, SystemInfo.GroupDriveCount, Drives
- Metrics: Total Drives Count, Largest Drive Size and Owner, Average Drive Contents Size, Total Size of All Drives
- Actionable Alerts: N/A
- Integration Mappings: Total Shared Drives, Shared Drives
Teams Inspector:
- Data Print Fields: Teams
- Metrics: Microsoft Teams: List of Archived Teams, Microsoft Teams: Count of Archived Teams, Microsoft Teams: List of Private Teams, Microsoft Teams: Count of Private Teams, Microsoft Teams: User Team Summary, Microsoft Teams: Channel Summary, Microsoft Teams: Teams Summary
- Actionable Alerts: Microsoft Teams: User Team Summary, Microsoft Teams: Channel Summary, Microsoft Teams: Teams Summary
- Integration Mappings: Active Teams, Archived Teams, Count of Private Channels, List of Private Channels, Teams
Updated 15 days ago